 Image: WhataWin
Image: WhataWinNew research from Palo Alto Networks’s Unit 42 exposes an progressive onslaught run successful which a menace histrion hunts for Amazon IAM credentials successful existent clip successful GitHub repositories and starts utilizing them little than 5 minutes later. The last payload runs customized Monero cryptomining bundle connected virtual machines deployed connected the Amazon instances.
Jump to:
- IAM credentials exposed connected GitHub
- Technical details astir this onslaught campaign
- The extremity of this onslaught campaign: Cryptomining
- GitHub’s automated measures for detecting secrets
- How to mitigate this cybersecurity risk
IAM credentials exposed connected GitHub
GitHub offers its users galore features for handling their codification wrong the platform. One of these features consists of providing a database of each nationalist repositories to immoderate idiosyncratic requesting it, which helps developers easy way assorted developments they are funny in. The tracking is done successful existent clip and allows anyone, including menace actors, to spot caller repositories arsenic soon arsenic they are being pushed to GitHub.
SEE: 8 Best Identity and Access Management (IAM) Solutions for 2023 (TechRepublic)
Palo Alto Networks’s Unit 42 researchers study that it is imaginable to find Amazon Web Services Identity and Access Management credentials wrong GitHub’s nationalist repositories and that these credentials are actively hunted for by cybercriminals.
To analyse the hazard deeper, the researchers decided to store IAM credentials connected GitHub and cheque each enactment astir it. That honeypot investigating revealed that leaked AWS keys that were encoded successful base64 and stored connected GitHub were not recovered oregon utilized by menace actors, who lone fetched wide substance AWS keys hidden down a past perpetrate successful a random file.
The honeypot enabled researchers William Gamazo and Nathaniel Quist to observe a peculiar onslaught run starting wrong 5 minutes aft the credentials were enactment connected GitHub.
Technical details astir this onslaught campaign
The campaign, dubbed EleKtra-Leak by the researchers successful notation to the Greek unreality nymph Electra and the usage of Lek arsenic the archetypal 3 characters successful the passwords utilized by the menace actor, has been progressive since astatine slightest December 2020, according to Unit 42.
Once IAM credentials are found, the attacker performs a bid of reconnaissance actions to cognize much astir the AWS relationship that is accessed (Figure A).
Figure A
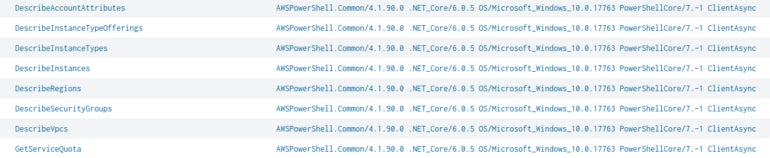 Reconnaissance actions tally by the menace histrion connected the AWS account. Image: Palo Alto Networks
Reconnaissance actions tally by the menace histrion connected the AWS account. Image: Palo Alto NetworksAfter those actions are done, the menace histrion creates caller AWS Security Groups earlier launching aggregate Amazon Elastic Compute Cloud instances per portion crossed immoderate accessible AWS region.
Gamazo and Quist could observe much than 400 API calls wrong 7 minutes, each done via a VPN connection, showing that the histrion has automated the onslaught against those AWS relationship environments.
The menace histrion aimed astatine large-format unreality virtual machines to execute their operations, arsenic those person higher processing power, which is what attackers are looking for erstwhile moving cryptomining operations. The menace histrion besides chose backstage images for Amazon Machine Images; immoderate of those images were aged Linux Ubuntu distributions, starring the researchers to judge the cognition dates backmost to astatine slightest 2020.
The menace histrion besides appeared to artifact AWS accounts that routinely exposure IAM credentials, arsenic this benignant of behaviour mightiness originate from menace researchers oregon honeypot systems.
The extremity of this onslaught campaign: Cryptomining
Once each the reconnaissance is done and virtual machines are launched, a payload is being delivered, downloaded from Google Drive. The payload, encrypted connected Google storage, is being decrypted upon download.
Unit 42 states the payload is simply a known cryptomining instrumentality seemingly utilized successful 2021 and reported by Intezer, a institution specializing successful autonomous Security Operation Systems platforms. In the reported onslaught campaign, Intezer indicated that a menace histrion had accessed exposed Docker instances connected the net to instal cryptomining bundle for mining Monero cryptocurrency. That customized cryptomining bundle is the aforesaid arsenic what is utilized successful the caller run exposed by Palo Alto Networks.
The bundle is configured to usage the SupportXMR mining pool. Mining pools let respective radical to adhd their computing clip to the aforesaid workspace, expanding their chances to gain much cryptocurrency. As stated by Palo Alto Networks, the SupportXMR work lone provides time-limited statistics, truthful the researchers pulled the mining statistic for respective weeks, arsenic the aforesaid wallet was utilized for the AWS mining operations (Figure B).
Figure B
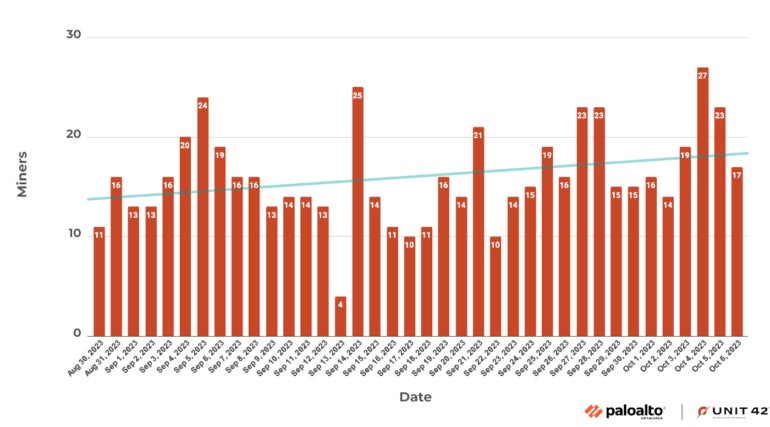 SupportXMR statistic associated with the menace actor’s wallet. Image: Palo Alto Networks
SupportXMR statistic associated with the menace actor’s wallet. Image: Palo Alto NetworksBetween Aug. 30, 2023 and Oct. 6, 2023, a full of 474 unsocial miners appeared, each 1 being a unsocial Amazon EC2 instance. It is not yet imaginable to get an estimation of the fiscal summation generated by the menace actor, arsenic Monero includes privateness controls limiting the tracking of this benignant of data.
GitHub’s automated measures for detecting secrets
GitHub automatically scans for secrets successful files stored connected the level and notifies work providers astir leaked secrets connected GitHub.
During their investigation, Gamazo and Quist noticed the secrets they were intentionally storing connected GitHub arsenic honeypot information for their probe were so successfully detected by GitHub and reported to Amazon, who successful crook automatically applied wrong minutes a quarantine policy that prevents attackers from performing operations specified arsenic accessing AWS IAM, EC2, S3, Lambda and Lightsail.
During the probe process, Unit 42 was leaving the quarantine argumentation successful spot and passively studying the attackers’ tests of the accounts; then, the argumentation was dropped to survey the full onslaught chain.
The researchers constitute that they “believe the menace histrion mightiness beryllium capable to find exposed AWS keys that aren’t automatically detected” and that according to their evidence, the attackers apt did, arsenic they could run the onslaught without immoderate interfering policy. They besides authorities that “even erstwhile GitHub and AWS are coordinated to instrumentality a definite level of extortion erstwhile AWS keys are leaked, not each cases are covered,” and that different imaginable victims of this menace histrion mightiness person been targeted successful a antithetic manner.
How to mitigate this cybersecurity risk
IAM credentials should ne'er beryllium stored connected GitHub oregon immoderate different online work oregon storage. Exposed IAM credentials should beryllium removed from repositories, and caller IAM credentials should beryllium generated to regenerate the leaked ones.
Businesses should usage short-lived credentials for performing immoderate dynamic functionality wrong a accumulation environment.
Security teams should show GitHub repositories utilized by their organizations. Auditing clone events that hap connected those repositories should beryllium done due to the fact that it is indispensable for menace actors to archetypal clone repositories to presumption their content. That diagnostic is disposable for each GitHub Enterprise accounts.
Custom dedicated scanning for secrets connected repositories should besides beryllium done constantly. Tools specified arsenic Trufflehog mightiness assistance with that task.
If determination is nary request to stock the organization’s repositories publicly, backstage GitHub repositories should beryllium utilized and lone accessed by the organization’s personnel. Access to the backstage GitHub repositories should beryllium protected by multifactor authentication to debar an attacker accessing them with leaked login credentials.
Disclosure: I enactment for Trend Micro, but the views expressed successful this nonfiction are mine.









 English (US) ·
English (US) ·