Australian identity entree management professionals person been urged to entrench individuality arsenic a instauration of their organisations’ cyber information posture, arsenic sub-par absorption of important exposures, including instrumentality identities, was putting galore organisations astatine risk.
Gartner VP expert Felix Gaehtgens, speaking astatine Gartner’s Security & Risk Management Summit successful Sydney, argued IAM practitioners should champion concern successful mature IAM programs, centred astir an individuality cloth attack wrong their organisations.
Organisations could heighten resilience done amended IAM hygiene, Gaehtgens said. He warned against allowing tech vendors to fastener information into silos and usage AI without getting the information close first. One proposition was to instrumentality a merchandise absorption attack to engaging antithetic stakeholders.
IAM present astatine the halfway of a mature cyber information posture
IAM leaders person faced a cardinal displacement successful the individuality scenery implicit the past fewer years, Gaehtgens said. This was chiefly owed to the world they were present “expected to make centralised power successful a wholly decentralised world” successful bid to support cyber security.
Employees moving from anyplace had eroded the worth of bequest information controls astatine the perimeter, Gaehtgens said, portion assets, information and applications were present being protected with antithetic types of entree controls — galore implemented by 3rd parties similar unreality vendors.
PREMIUM: Consider creating a cloud information policy.
“The CISO is asked 3 main questions by the board: ‘Are we secure?’, ‘Are we compliant?’ and ‘What astir AI?’” Gaehtgens said. “IAM is astatine the centre of each this. The relation is becoming overmuch much important. Why? Because it is astatine the centre of information successful the caller world.”
The emergence of instrumentality identities
The maturation of instrumentality identities, successful summation to quality identities, had go a “big problem,” Gaehtgens said. There are present betwixt 10 and 45 times arsenic galore instrumentality identities successful an organisation, galore of them heavy privileged, making them a huge, unmanaged cyber risk.
Organisations should enactment individuality archetypal with mature IAM program
Moving individuality to the centre of cyber information is key, Gaehtgens said.
“Many of you person a batch of tools but don’t truly person a good, functioning IAM programme — present is your opportunity,” said Gaehtgens. “It is the power level and instauration of cyber information — this is wherever absorption request to be.”
IAM programs should marque individuality absorption “consistent, contextual and continuous” and beryllium enabled by IAM leaders consenting to physique relationships extracurricular of IT.
Consistent
According to Gaehtgens, planetary regulations are designed to support idiosyncratic information wherever it whitethorn be, including successful databases, unstructured files, successful question oregon astatine rest. Gaehtgens said this means that, portion organisations person a slew of tools, they request consistency successful the entree policies applied.
Contextual
Policies request to beryllium dynamic and context-aware.
“Just due to the fact that idiosyncratic tin entree a folder doesn’t mean they should beryllium downloading 30 documents a infinitesimal — that’s not emblematic for a quality being, and mightiness bespeak their relationship has been taken implicit by a bot,” Gaehtgens said.
Continuous
The aboriginal volition spot continuous adaptive spot applied passim sessions. Gaehtgens said azygous sign-off was coming, which would impact the quality to terminate aggregate sessions crossed systems based connected idiosyncratic events, thing helium said would go mean for users.
Leadership
To enactment successful spot an IAM program, IAM leaders volition request to fortify relationships beyond IT. Gaehtgens urged IAM leaders to larn the connection of business, including concern and legal, truthful they tin measurement and pass astir IAM successful presumption similar concern worth and risk.
SEE: A apical IAM solution tin assistance fortify cyber information efforts.
Success could beryllium easier with a merchandise absorption approach. Gaehtgens said determination is simply a inclination towards merchandise absorption approaches to IAM programs, which is starring to an acceleration successful concern worth and transportation done a “highly cross-functional” style.
Focus connected individuality cloth alternatively than IAM tools
A much cohesive, architecturally dependable mode of managing IAM is needed for the future, Gaehtgens said.
“Most organisations conflict with the transportation of basal IAM capabilities for humans and machines, adjacent aft years of concern successful and enactment connected this,” said Gaehtgens.
Embracing an individuality cloth architectural approach
An “identity fabric” attack could assistance IAM pros pat into their existent opportunities and escaped themselves from the shackles of vendor lock-in, Gaehtgens said. He enactment guardant a model of 10 principles Gartner uses to usher clients towards an individuality cloth exemplary (Figure A).
 Figure A: Gartner’s 10 individuality cloth principles let organisations to physique Identity Access Management capabilities for a decentralised world. Image: Gartner
Figure A: Gartner’s 10 individuality cloth principles let organisations to physique Identity Access Management capabilities for a decentralised world. Image: GartnerThese see expanding the scope to include:
- Machine identities, liable for galore “credential leakage takeovers.”
- Event-based connectivity, alternatively than static batch analysis
- Composable “and, successful the agelong run, compostable” architecture that tin flex done change.
Working with topology could alteration organisations to summation centralised power successful a decentralised situation by ripping functions retired of tools with an abstraction layer. This sees the functions of underlying tools connected astatine a higher level to orchestrate them for antithetic usage cases.
AI capabilities could boost IAM squad productivity
AI is apt to instrumentality connected aspects of IAM, specified arsenic relationship takeover detection and idiosyncratic entity behaviour analytics. It could besides urge right-sized entree policies from entitlement information oregon assistance integrate applications with IAM services, including coding and configuration updates.
Gaehtgens cautioned that the information needed to beryllium right, and information absorption and engineering could go a ceremonial capableness for an IAM program.
“AI tin present immoderate worth arsenic agelong arsenic you besides enactment connected the indispensable information absorption and information engineering dependencies,” Gaehtgens said.
Identity hygiene the archetypal enactment of cyber information defence
IAM is “the archetypal enactment of defence successful reducing the fig of alerts going done to your (security operations centre),” Gaehtgens said. This means IAM professionals request to absorption connected individuality hygiene to boost prevention and detection, including with instrumentality identities.
SEE: Explore the quality betwixt IAM and PAM solutions
IAM teams tin commencement with little effort activities specified arsenic relationship beingness (Figure B). However, Gaehtgens said portion Australia’s Essential Eight framework recommends tackling instrumentality identities astatine Maturity Level 3, it should beryllium thing organisations look astatine earlier then.
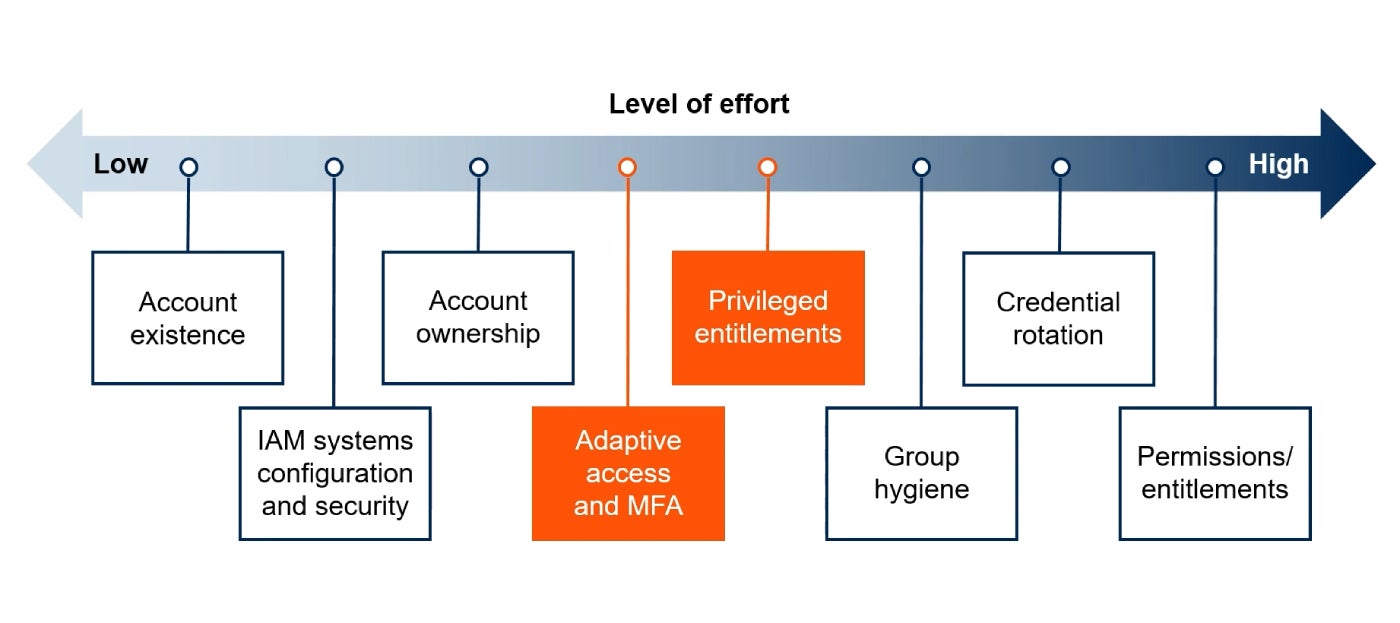 Figure B: IAM professionals tin prosecute a scope of activities that volition get their organisations person to bully individuality hygiene. Image: Gartner
Figure B: IAM professionals tin prosecute a scope of activities that volition get their organisations person to bully individuality hygiene. Image: GartnerHe recommended IAM configuration vigilance.
“I’ve seen unrecorded IAM systems configured with privileged entree for investigating thing that was ne'er removed,” Gaehtgens said. “If anyone got upwind of that, they could instrumentality implicit that IAM strategy and could alteration the roles to immoderate they wanted.”
IAM teams could besides prosecute activities with mid-level of effort, similar rolling retired adaptive entree and MFA.
“The cardinal is equilibrium betwixt concern successful hygiene and menace detection and response,” Gaehtgens said. “The amended we are astatine prevention, the little comes done for detection.”









 English (US) ·
English (US) ·