Google Cloud’s squad precocious spoke astir the astir notable cybersecurity threats of 2023 — multi-faceted extortion and zero-day exploitation — and predicted much zero-day attacks successful 2024, during 2 public, virtual sessions. Plus, Google predicts that some attackers and defenders volition proceed to usage generative AI. However, generative AI astir apt won’t make its ain malware successful 2024.
Two astir notable cybersecurity threats of 2023
The 2 astir notable cybersecurity threats of 2023, according to Google Cloud’s Luke McNamara, main spot and information analyst, were multi-faceted extortion (also known arsenic treble extortion) and zero-day exploitation.
Multi-faceted exploitation
Multi-faceted exploitation includes ransomware and information theft, though the fig of ransomware attacks tracked by Google Cloud fell successful 2023. The astir communal ransomware families utilized successful multi-faceted exploitation attacks were LockBit, Clop and ALPHV.
Most ransomware attacks initially stemmed from stolen credentials. Brute unit attacks and phishing were the adjacent astir communal archetypal corruption vectors for ransomware.
SEE: Know the informing signs if idiosyncratic other has accessed your Google account. (TechRepublic)
Attackers progressively enactment stolen credentials up for merchantability connected information leak sites, McNamara said. “This past 4th (Q3 2023) we saw the highest fig of postings to DLS sites since we started tracking this successful 2020,” McNamara said.
Many attackers are industry-agnostic, but “Quarter implicit quarter, manufacturing seems to beryllium peculiarly deed and impacted disproportionately,” McNamara said. “That’s wherever we’re seeing a batch of the enactment successful presumption of volume.”
Zero-day exploitation
Zero-day exploitation is defined by Google Cloud arsenic vulnerabilities with nary known patches that menace actors are actively exploiting. In 2023, Google Cloud Security tracked 89 specified attacks (Figure A), surpassing the erstwhile precocious of 2021.
Figure A
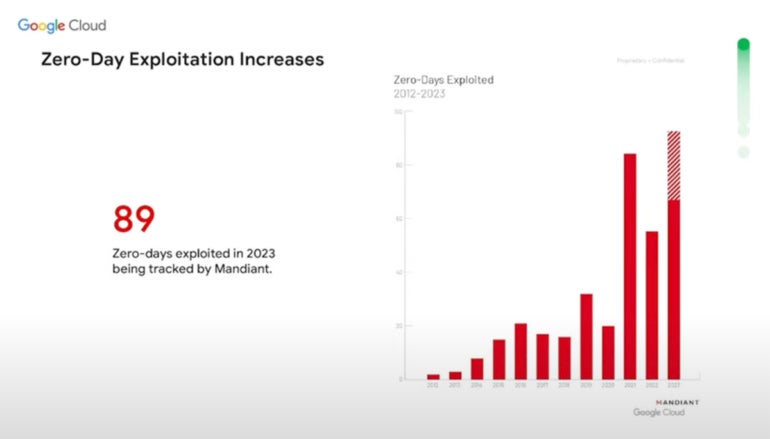 The maturation successful zero-day attacks from 2012 to 2023 according to Mandiant. Mandiant is owned by Google. Image: Mandiant/Google Cloud
The maturation successful zero-day attacks from 2012 to 2023 according to Mandiant. Mandiant is owned by Google. Image: Mandiant/Google CloudMany zero-day threats are nation-state affiliated oregon sponsored. The 2nd astir communal information among menace actors utilizing zero-day threats is to get money.
SEE: What the Cisco Talos Year successful Review study revealed (TechRepublic)
Google Cloud’s 2024 cybersecurity forecast
Andrew Kopcienski, main menace quality expert astatine Google’s Mandiant Communication Center, talked astir nation-state menace actors, zero-day attacks, question betwixt unreality environments and credential theft during his presumption astir cyber threats successful 2024. In particular, China and Russia are focusing connected zero-day attacks, helium said.
“We afloat expect to spot a batch much zero time usage successful 2024 by not conscionable nation-state sponsored attackers but cyber criminals arsenic well,” said Kopcienski. “Zero days are 1 of the champion methods attackers person to stay undetected erstwhile they get into a network.”
China-sponsored menace actors
China-sponsored actors person focused connected processing capabilities successful uncovering and utilizing zero days and botnets to stay undetected, Kopcienski said. Google Cloud expects China’s cyber menace efforts to absorption connected high-tech fields similar spot development.
Russian-sponsored espionage
Russian espionage focused connected Ukraine has been a problem, helium said. Google Cloud recovered Russia has conducted campaigns extracurricular Ukraine arsenic well, but those mostly absorption connected gaining strategical accusation regarding Ukraine, Kopcienski said. Russian-sponsored attackers usage “living disconnected the land” attacks that bash not necessitate malware; instead, they maltreatment autochthonal capabilities, and their postulation looks similar autochthonal traffic. Google Cloud expects much attacks from Russian-backed actors successful 2024, mostly focused connected victims wrong Ukraine oregon related to Ukraine.
North Korean-sponsored menace actors
Google Cloud besides looked intimately astatine nation-state actors associated with North Korea.
“They person developed a scrappy capableness to motorboat bundle proviso concatenation attacks,” Kopcienski said.
North Korea was the archetypal known nation-state histrion to usage “cascading” bundle proviso concatenation attacks, which piggybacked disconnected each other. Many of these attacks are astir stealing cryptocurrency oregon companies conducting cryptocurrency operations. Google Cloud expects to spot North Korea-affiliated menace actors’ attacks broaden successful 2024.
Credential theft and extortion
Another interest for 2024 is extortion. “Credential theft (Figure B) is the sanction of the crippled … that has go the astir drastic and astir fashionable measurement a batch of these attackers are using,” Kopcienski said.
Figure B
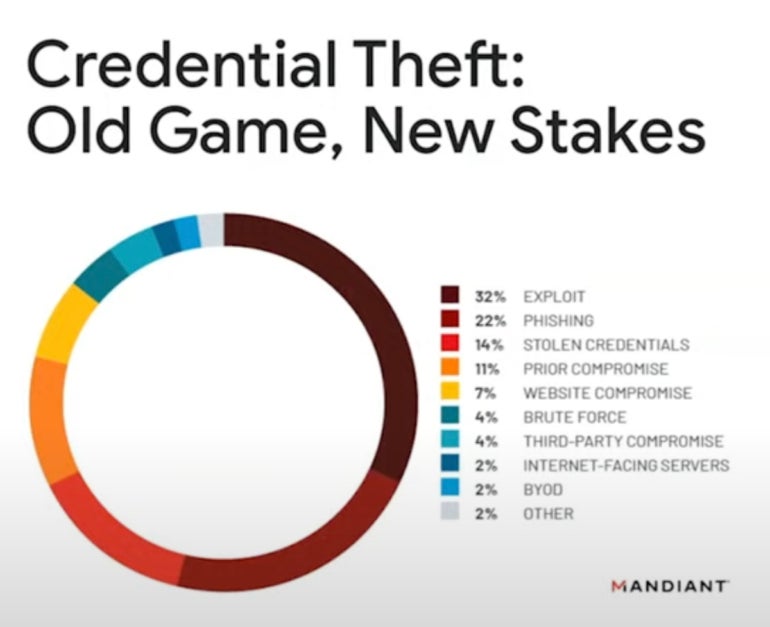 Mandiant’s probe shows that credential theft originates from a assortment of vectors. Image: Mandiant/Google Cloud
Mandiant’s probe shows that credential theft originates from a assortment of vectors. Image: Mandiant/Google Cloud“Into 2024, we expect to spot a absorption connected information leak sites, particularly by extortion actors,” helium said.
Movement betwixt unreality environments
Attackers successful 2024 whitethorn usage tactics, techniques and procedures that let them to question crossed antithetic unreality environments, apt owed to the expanding usage of unreality and hybrid environments.
How generative AI has and volition impact cybersecurity successful 2023 and 2024
Attackers tin usage generative AI to make text, dependable messages and imagery, and Google Cloud expects this to go much common.
“AI is enabling peculiar kinds of malicious attackers, mostly successful disinformation campaigns. We are precise acrophobic going into adjacent twelvemonth astir the interaction of disinformation that has been augmented by AI, particularly erstwhile it comes to the 2024 election,” said Kopcienski.
In 2023, generative AI has been utilized by attackers and defenders. In 2024, AI whitethorn beryllium utilized to summation the standard of attacks, specified arsenic by adopting AI successful telephone centers moving ransomware negotiations.
Generative AI mightiness beryllium capable to make malware astatine immoderate constituent successful the future, but Kopcuenski said not to expect that to hap arsenic soon arsenic 2024. He recommends cybersecurity professionals “remain grounded” and not suffer slumber erstwhile it comes to generative AI. Many of its threats are “hypothetical,” helium said.
“There’s a batch of hype and disinformation retired determination already astir what AI tin and can’t do. … (AI is) not an overwhelming gyration successful presumption of the threats being posed,” helium said.









 English (US) ·
English (US) ·