A caller study from Palo Alto Networks’s Unit 42 exposes the persistent and evolving menace of DNS hijacking, a stealthy maneuver cybercriminals usage to reroute net traffic. By leveraging passive DNS analysis, the cybersecurity institution besides provided real-world examples of caller DNS hijacking attacks — highlighting the urgency of countering this hidden danger.
What is DNS hijacking?
DNS hijacking involves modifying the responses from targeted DNS servers, redirecting users to attacker-controlled servers alternatively of the morganatic ones they mean to reach.
DNS hijacking tin beryllium done successful respective ways:
- Gaining power of the domain owner’s account, providing entree to DNS server settings: In this scenario, the attacker possesses valid idiosyncratic credentials with the authorization to straight alteration the DNS server configuration. The attacker could besides person valid credentials for the domain registrar oregon DNS work supplier and alteration the configuration.
- DNS cache poisoning: The attacker impersonates a DNS nameserver and forges a reply, starring to attacker-controlled contented alternatively of the morganatic one.
- Man-in-the-Middle attack: The attacker intercepts the user’s DNS queries and provides results that redirect the unfortunate to the attacker-controlled content. This lone works if the attacker is successful power of a strategy implicated successful the DNS query/answer process.
- Modifying DNS-related strategy files, specified arsenic the big record successful Microsoft Windows systems. If the attacker has entree to that section file, it is imaginable to redirect the idiosyncratic to attacker-controlled content.
Attackers mostly usage DNS hijacking to redirect users to phishing websites that look akin to the intended websites oregon to infect the users with malware.
Detecting DNS hijacking with passive DNS
The Unit 42 study described a method to observe DNS hijacking via passive DNS analysis.
What is passive DNS?
Passive DNS describes terabytes of humanities DNS queries. In summation to the domain sanction and the DNS grounds type, passive DNS records mostly incorporate a “first seen” and a “last seen” timestamp. These records let users to hint the IP addresses a domain has directed users to implicit time.
For an introduction to look successful passive DNS, it indispensable beryllium queried by a strategy whose DNS queries are recorded by passive DNS systems. This is wherefore the astir broad passive DNS accusation mostly comes from providers with precocious query volumes, specified arsenic ISPs oregon companies with extended lawsuit bases. Subscribing to a passive DNS supplier is often advisable, arsenic they cod much DNS queries than the mean company, offering a much implicit presumption than section DNS queries alone.
SEE: Everything You Need to Know astir the Malvertising Cybersecurity Threat (TechRepublic Premium)
Detecting DNS hijacking
Palo Alto Network’s method for detecting DNS hijacking begins by identifying never-seen-before DNS records, arsenic attackers often make caller records to redirect users. Never-seen-before domain names are excluded from detection due to the fact that they deficiency capable humanities information. Invalid records are besides removed astatine this step.
The DNS records are past analyzed utilizing passive DNS and geolocation information based connected 74 features. According to the report, “some features comparison the humanities usage of the caller IP code to the aged IP code of the domain sanction successful the caller record.” The extremity is to observe anomalies that could bespeak a DNS hijack operation. A machine-learning exemplary past provides a probability people based connected the analysis.
WHOIS records are besides checked to forestall a domain from being re-registered, which mostly leads to a implicit IP code alteration that could beryllium detected arsenic DNS hijack.
Finally, progressive navigations are conducted connected the domains’ IP addresses and HTTPS certificates. Identical results bespeak mendacious positives and tin truthful beryllium excluded from DNS hijacking operations.
DNS hijack statistics
From March 27 to Sept. 21 2024, researchers processed 29 cardinal caller records, 6,729 of which were flagged arsenic DNS hijacking. This resulted successful an mean of 38 DNS hijack records per day.
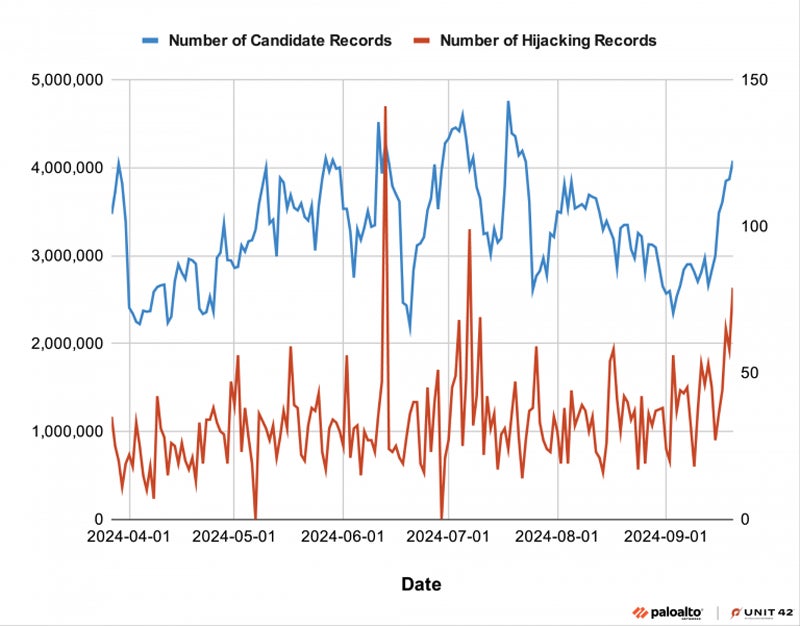 Daily counts of candidates and predicted DNS hijacking records. Image: Palo Alto Networks
Daily counts of candidates and predicted DNS hijacking records. Image: Palo Alto NetworksUnit 42 indicates that cybercriminals person hijacked domains to big phishing content, deface websites, oregon dispersed illicit content.
DNS hijacking: Real-world examples
Unit 42 has seen aggregate DNS hijack cases successful the wild, mostly for cybercrime purposes. Yet it is besides imaginable to usage DNS hijacking for cyberespionage.
Hungarian governmental enactment leads to phishing
One of the largest governmental absorption groups to the Hungarian government, the Democratic Coalition (DK), has been hosted connected the aforesaid subnet of IP addresses successful Slovakia since 2017. In January 2024, researchers detected a alteration successful the DK’s website, which abruptly resolved to a caller German IP address, starring to a Microsoft login leafage alternatively of the governmental party’s accustomed quality page.
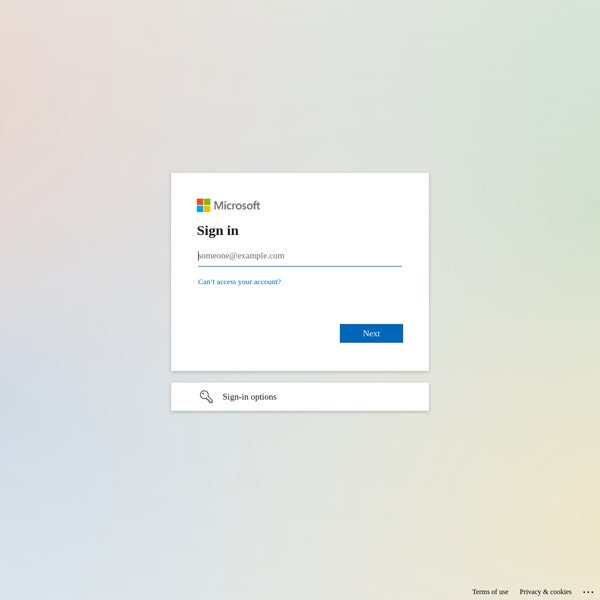 Microsoft login phishing page. Image: Palo Alto Networks
Microsoft login phishing page. Image: Palo Alto NetworksUS institution defaced
In May 2024, 2 domains of a starring U.S. inferior absorption institution were hijacked. The FTP service, which has led to the aforesaid IP code since 2014, abruptly changed. The DNS nameserver was hijacked utilizing the attacker-controlled ns1.csit-host.com.
According to the research, the attackers besides utilized the aforesaid nameservers to hijack different websites successful 2017 and 2023. The extremity of the cognition was to amusement a defaced leafage from an activistic group.
How companies tin support themselves from this threat
To support from these threats, the study suggested that organizations:
- Deploy multi-factor authentication to entree their DNS registrar accounts. Establishing a whitelist of IP addresses allowed to entree DNS settings is besides a bully idea.
- Leverage a DNS registrar that supports DNSSEC. This protocol adds a furniture of information by digitally signing DNS communications, making it much hard to intercept and spoof information for menace actors.
- Use networking tools that comparison DNS queries results from third-party DNS servers — specified arsenic those from ISPs — to the DNS queries results obtained erstwhile utilizing the company’s accustomed DNS server. A mismatch could bespeak a alteration successful DNS settings, which mightiness beryllium a DNS hijacking attack.
In addition, each hardware, specified arsenic routers, indispensable person up-to-date firmware, and each bundle indispensable beryllium up-to-date and patched to debar being compromised by communal vulnerabilities.
Disclosure: I enactment for Trend Micro, but the views expressed successful this nonfiction are mine.







 English (US) ·
English (US) ·