Think astir your slope accounts, work-related sites, societal media, online retail accounts, unreality services, question sites and edifice sites — each 1 apt requires a login and password. When I compiled each my accounts, passwords and pins a twelvemonth ago, I realized I had much than 200 logins.
To support track, astir users reuse the aforesaid passwords implicit and over. However, that poses a large threat. If a hacker gains entree to 1 account, they tin usage the aforesaid credentials to entree galore much accounts.
Cybersecurity experts are adamant that each password should beryllium unsocial and of an due magnitude and configuration. That’s wherever password managers travel in.
1Password's high-end encryption, zero-knowledge architecture and regular information audits marque it a reliable and harmless mode to securely store logins and passwords. You tin larn much astir 1Password and research pricing and program details connected its site.
Jump to:
- What is simply a password manager?
- Types of password managers
- How bash password managers work?
- Password manager benefits vs. password manager drawbacks
- Key password manager features
- How unafraid are password managers?
- Popular password managers
- Should your enactment usage a password manager?
What is simply a password manager?
A password manager is fundamentally an encrypted vault for storing passwords that is itself protected by a maestro password. To summation entree to the passwords stored successful the manager, a idiosyncratic has to cognize the maestro password; successful galore cases, a 2nd authentication origin is required, specified arsenic a codification oregon a biometric input.
Password managers tin beryllium utilized to store passwords for casual recall, but 1 of the champion features of astir password managers is their quality to make passwords. A longer password is much unafraid and harder to crack, and the passwords generated by password managers are combinations of random numbers and letters that are precise secure.
Another important diagnostic of astir password managers is the quality to automatically capable successful passwords for stored sites. By utilizing that feature, you won’t person to benignant thing but the maestro password, and it’s besides a bully mode to debar having passwords stolen by keylogging malware.
Furthermore, a bully password manager allows you to sync your information betwixt devices truthful you won’t person to interest astir losing accusation stored connected your desktop if you’re utilizing your smartphone, for example.
Password managers instrumentality the hassle retired of integer beingness by putting each delicate credential accusation successful 1 secure, easy-to-access location.
Types of password managers
Be aware, though, determination are galore antithetic types of password managers. There are solutions designed for individuals, families oregon tiny businesses and determination are those solely for enterprises. Organizations should debar the user versions and opt for those that connection endeavor features arsenic good arsenic the quality to negociate each business-related passwords for each user.
Enterprise-class tools tin power and unafraid credentials for immoderate and each privileged accounts, services, systems and applications. As such, these tools tin differentiate betwixt the antithetic levels of entree that whitethorn beryllium wrong an organization, adhd other layers of extortion to privileged accounts and enforce argumentation crossed the enactment arsenic to erstwhile passwords indispensable beryllium changed, arsenic good arsenic their magnitude and configuration (capitals, lowercase, numbers, symbols, etc.).
Cloud vs. section password managers
In summation to the favoritism betwixt endeavor and user tools, determination are besides password managers that store passwords connected a section instrumentality oregon server and those that store them successful the cloud.
There are pros and cons to some options:
- Storing your passwords successful the unreality allows the passwords to sync seamlessly betwixt devices.
- Cloud retention eliminates the interest that you volition suffer your stored passwords if your machine crashes.
- Storing passwords locally prevents information theft successful the lawsuit of a unreality retention breach.
- Local password retention could pb to a stolen machine being utilized to summation entree to each your accounts.
Most password managers that utilize the unreality tin person their sync functions disabled if needed to debar the hazard inherent successful unreality storage. The aforesaid isn’t existent for section retention options, though: If you question retired an enactment with a section password vault, you won’t beryllium capable to sync it to the cloud.
Shared relationship password absorption is not a benignant of password manager
There is often disorder astir whether to usage a password manager oregon shared relationship password absorption (SAPM). Both are chiseled and person antithetic roles successful the enterprise, and some tin relation broadside by side. Password managers are designed to store and springiness casual entree to idiosyncratic accounts; these tools shouldn’t beryllium utilized to store head credentials, shared accounts oregon different concern accounts that aren’t assigned solely to 1 user.
SAPM is designed to negociate and power shared accounts. Depending connected the SAPM product, shared relationship passwords are either fixed retired erstwhile a idiosyncratic signs successful and are reset aft logout oregon the passwords are obscured from a idiosyncratic truthful they tin usage the privileged relationship without ever knowing the password. It is simply a bully thought for ample businesses with shared privileged accounts (domain admins, root, etc.) to instrumentality an SAPM merchandise on with a password manager. Corporate password absorption tools tin store credentials for important websites and beryllium linked to Active Directory, making the full process a azygous sign-on.
Whatever signifier of password manager is utilized, the extremity is to destruct atrocious habits similar utilizing the aforesaid password for aggregate accounts, utilizing elemental passwords and penning them down connected sticky notes, spreadsheets oregon connection documents. If long, analyzable passwords are used, it besides greatly reduces the atrocious signifier of users giving idiosyncratic other their password, thereby reducing the hazard of a information breach.
How bash password managers work?
Enterprise password managers trim the risks associated with credential compromise by safeguarding entree to relationship passwords and assorted types of authentication credentials, specified arsenic Secure Shell keys. This provides IT oregon information absorption with implicit power implicit some strategy and exertion entree done what is known arsenic unrecorded league management. Administrators are past capable to monitor, detect, record, fastener and papers suspicious behavior. Enterprise-class password absorption tools besides springiness them the quality to terminate sessions for circumstantial users if anomalous behaviour oregon postulation is detected.
Automation and monitoring features wrong password managers support way of the passwords successful usage and supply the means to enforce beardown password policies for some humans and machines. For example, if the enactment requires definite accounts to alteration their passwords each period oregon each quarter, the strategy sends retired automatic messages to pass users and includes policing features to enforce compliance.
Password manager benefits vs. password manager drawbacks
Figure A
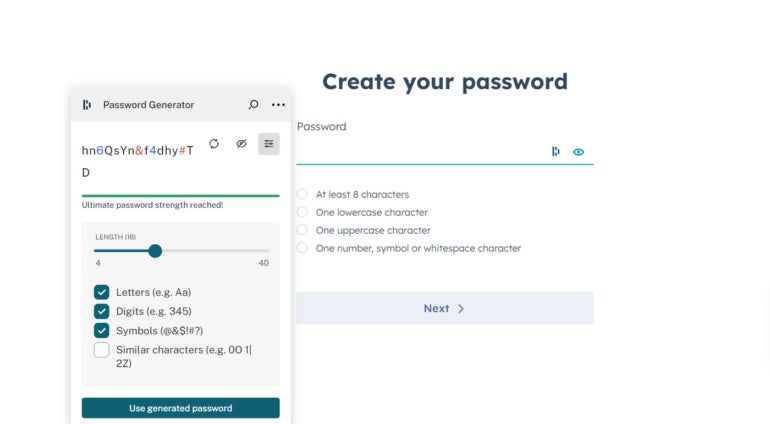 Dashlane password generator. Image: Dashlane
Dashlane password generator. Image: DashlanePerhaps the top payment of a password manager is the quality to enforce password hygiene by making each users usage analyzable and lengthy passwords that are hard to hack. That said, the top drawback of password managers is that they tin enactment arsenic azygous points of failure. By knowing the maestro password, idiosyncratic tin past entree each different linked accounts.
| Enforcement of password hygiene. | Single constituent of failure. |
| Use of agelong and analyzable passwords. | Anyone with the maestro password tin entree each different accounts. |
| Passwords that are astir intolerable to hack by brute unit techniques. | Users whitethorn beryllium unhappy with agelong analyzable passwords. |
| A assortment of information features tin beryllium incorporated into password managers. | Users whitethorn look further authentication methods. |
Key password manager features
Password managers that cater to ample enterprises and connection the astir information features are typically the astir expensive. Therefore, if a password manager is free, you tin expect it to beryllium stripped down to the basics and missing cardinal capabilities that enterprises need. Don’t expect overmuch successful the mode of security, either.
Here are immoderate cardinal features to expect successful an effectual password manager:
Enterprise management
There are galore user password managers around. They are large for individuals, families and tiny businesses. But user password managers deficiency the absorption capabilities that organizations request — specified arsenic password monitoring and enforcement passim an organization, requirements to alteration passwords according to a definite timeline and the quality to enforce compliance for password magnitude and configuration. Hence, you volition wage much for enterprise-class tools compared to thing much aimed astatine the user market.
Security
There are assorted information capabilities that are added by vendors to safeguard their password systems. These see multi-factor authentication, encryption, SSH keys and the quality to observe anomalous behaviour and fastener down systems. Some password absorption systems connection none, immoderate connection 1 oregon much and a fewer connection each of them. Pricing is impacted by the information diagnostic set. Some vendors complaint other for information add-ons and options. Others bundle information into the wide price.
AI and analytics
AI has taken the satellite by storm. Password absorption vendors person taken note. They are adding AI to their tools to observe unusual behaviour that whitethorn bespeak an attempted breach. They show idiosyncratic behaviour to urge the champion mode to set policy, dictate grooming and show password compliance. AI and analytics features are typically options you wage much for. However, immoderate vendors person begun to see them successful their wide price.
Data privacy
Data privateness and sovereignty are blistery topics close now. Many countries and regions person implemented pugnacious laws that tin levy hefty fines if information is transmitted extracurricular of their jurisdiction. Therefore, password managers should see features that alteration them to comply with exertion laws pertaining to privateness and sovereignty.
How unafraid are password managers?
Most password managers worthy utilizing utilize AES-256, which is mostly considered 1 of the strongest forms of encryption disposable — truthful beardown that the US authorities uses it to transmit top-secret information. However, determination are tools astir that either omit encryption oregon permission it up to the idiosyncratic to instrumentality it.
The likelihood of a hacker attacking your instrumentality and stealing information from your password absorption app are slim, and it’s adjacent slimmer that they’ll beryllium capable to decrypt that data. A mates of years ago, a information designer recovered it would instrumentality one cardinal years to brute-force ace AES-256 encryption. However, arsenic hackers utilize the processing powerfulness of modern GPUs and harness AI successful their nefarious efforts, that clip nexus has shrunk considerably and continues to bash so. Hence, passwords are getting longer and much analyzable to thwart adjacent the champion hackers. But the clip it takes idiosyncratic to ace a password shrinks to zero if the hacker has your maestro password and you aren’t utilizing two-factor authentication, truthful beryllium definite to favour password managers that connection MFA arsenic an other furniture of security.
SEE: All of TechRepublic’s cheat sheets and astute person’s guides
As with immoderate technology, thing is foolproof. Hackers person gained entree to the databases of password absorption companies and made disconnected with idiosyncratic information before, and it’s wholly imaginable that it could hap again.
What’s important to enactment isn’t the incidents that person compromised idiosyncratic security, though — it’s the alternative. Storing your passwords successful a web browser means the information is unsecured. If the hacker gets into your computer, those passwords are compromised and tin beryllium utilized to entree slope accounts and different delicate files.
Password managers are the champion mode to support way of each your net logins. You won’t find a amended mode to safeguard your information, adjacent with immoderate perceived flaws. When password managers see MFA, encryption and different information safeguards, the chances of compromise driblet dramatically.
Popular password managers
The bully quality is that determination are galore fantabulous enterprise password managers out there. They see the features that enterprises demand, arsenic good arsenic plentifulness of information safeguards.
- LastPass.
- Dashlane.
- 1Password.
- RoboForm.
- Keeper.
- Zoho Vault.
- Bitwarden.
- Okta.
- Auth0.
- SAP Single Sign-On.
- OneLogin.
Should your enactment usage a password manager?
The bottommost enactment is that nary endeavor funny successful keeping its information and applications unafraid should ever beryllium without a password absorption system. Those failing to bash truthful are mounting themselves up for the inevitability of ransomware attacks, malware infections and embarrassing headlines astir the authorities of their security.









 English (US) ·
English (US) ·