A menace histrion softly spent the past 2 years integrating themself successful the halfway squad of maintainers of XZ Utils, a escaped bundle command-line information compressor wide utilized successful Linux systems. The attacker dilatory managed to integrate a backdoor successful the bundle that was designed to interfere with SSHD and let distant codification execution via an SSH login certificate. The backdoor was discovered a fewer days earlier being released connected respective Linux systems worldwide.
The menace histrion is suspected to beryllium a developer with oregon utilizing the sanction Jian Tan. Several information experts judge this proviso concatenation onslaught mightiness beryllium authorities sponsored.
What is XZ Utils, and what is the XZ backdoor?
XZ Utils and its underlying room liblzma is simply a escaped bundle instrumentality that implements some XZ and LZMA, which are 2 compression/decompression algorithms wide utilized successful Unix-based systems, including Linux systems. XZ Utils is utilized by galore operations connected those systems for compressing and decompressing data.
The CVE-2024-3094 backdoor recovered successful XZ Utils was implemented to interfere with authentication successful SSHD, the OpenSSH server bundle that handles SSH connections. The backdoor enabled an attacker to execute distant codification via an SSH login certificate. Only XZ Utils versions 5.6.0 and 5.6.1 are impacted.
How the XZ backdoor was implemented cautiously for much than years
On March 29, 2024, Microsoft bundle technologist Andres Freund reported the find of the backdoor. He recovered it erstwhile helium became funny successful unusual behaviour of a Debian sid installation, specified arsenic SSH logins taking a batch of CPU and Valgrind errors and decided to analyse the symptoms successful depth. Freund explained that the find of the backdoor successful XZ was luck, arsenic it “really required a batch of coincidences.”
Yet it appears that the implementation of the backdoor has been a precise quiescent process that took astir 2 years. In 2021, a developer named Jian Tan, username JiaT75, appeared retired of the bluish to commencement moving connected the XZ Utils code, which is not antithetic due to the fact that developers of escaped bundle often enactment unneurotic connected updating code. Tan contributed often to the XZ task since precocious 2021, dilatory gathering spot successful the community.
In May 2022, an chartless idiosyncratic utilizing the fake sanction Dennis Ens complained connected the XZ mailing list that the bundle update was not satisfying. Another chartless user, Jigar Kumar, came into the treatment two times to unit the main developer of XZ Utils, Lasse Collin, to adhd a maintainer to the project. “Progress volition not hap until determination is caller maintainer,” Jigar Kumar wrote. “Why hold until 5.4.0 to alteration maintainer? Why hold what your repo needs?”
Meanwhile, Collin expressed that “Jia Tan has helped maine off-list with XZ Utils and helium mightiness person a bigger relation successful the aboriginal astatine slightest with XZ Utils. It’s wide that my resources are excessively constricted (thus the galore emails waiting for replies) truthful thing has to alteration successful the agelong term.” (Collin wrote Jia successful his connection portion different messages notation Jian. To adhd to the confusion, Jian’s nickname is JiaT75.)
In the months that followed, Tan became progressively progressive successful XZ Utils and became co-maintainer of the project. In February 2024, Tan issued commits for versions 5.6.0 and 5.6.1 of XZ Utils, some of which contained the backdoor.
It is besides absorbing to enactment that successful July 2023, Tan requested to disable ifunc (GNU indirect function) connected oss-fuzz, a nationalist instrumentality made to observe bundle vulnerabilities. That cognition was astir apt done to let the backdoor successful XZ to enactment undetected erstwhile it was released, arsenic the backdoor makes usage of that relation to execute its goals.
Finally, respective persons liable for antithetic Linux distributions person been contacted by the attacker to see the backdoored versions of XZ Utils successful their ain distributions. Richard WM Jones from RedHat wrote astir it connected a forum: “Very annoying – the evident writer of the backdoor was successful connection with maine implicit respective weeks trying to get xz 5.6.x added to Fedora 40 & 41 due to the fact that of it’s ‘great caller features’. We adjacent worked with him to hole the valgrind contented (which it turns retired present was caused by the backdoor helium had added). We had to contention past nighttime to hole the occupation aft an inadvertent interruption of the embargo. He has been portion of the xz task for 2 years, adding each sorts of binary trial files, and to beryllium honorable with this level of sophistication I would beryllium suspicious of adjacent older versions of xz until proven otherwise”. Tan besides tried to person it included successful Ubuntu.
XZ backdoor: A highly method attack
In summation to the highly elaborated societal engineering covered antecedently successful this article, the backdoor itself is precise complex.
Microsoft’s elder menace researcher Thomas Roccia designed and published an infographic to amusement the full cognition starring to CVE-2024-3094 (Figure A).
Figure A
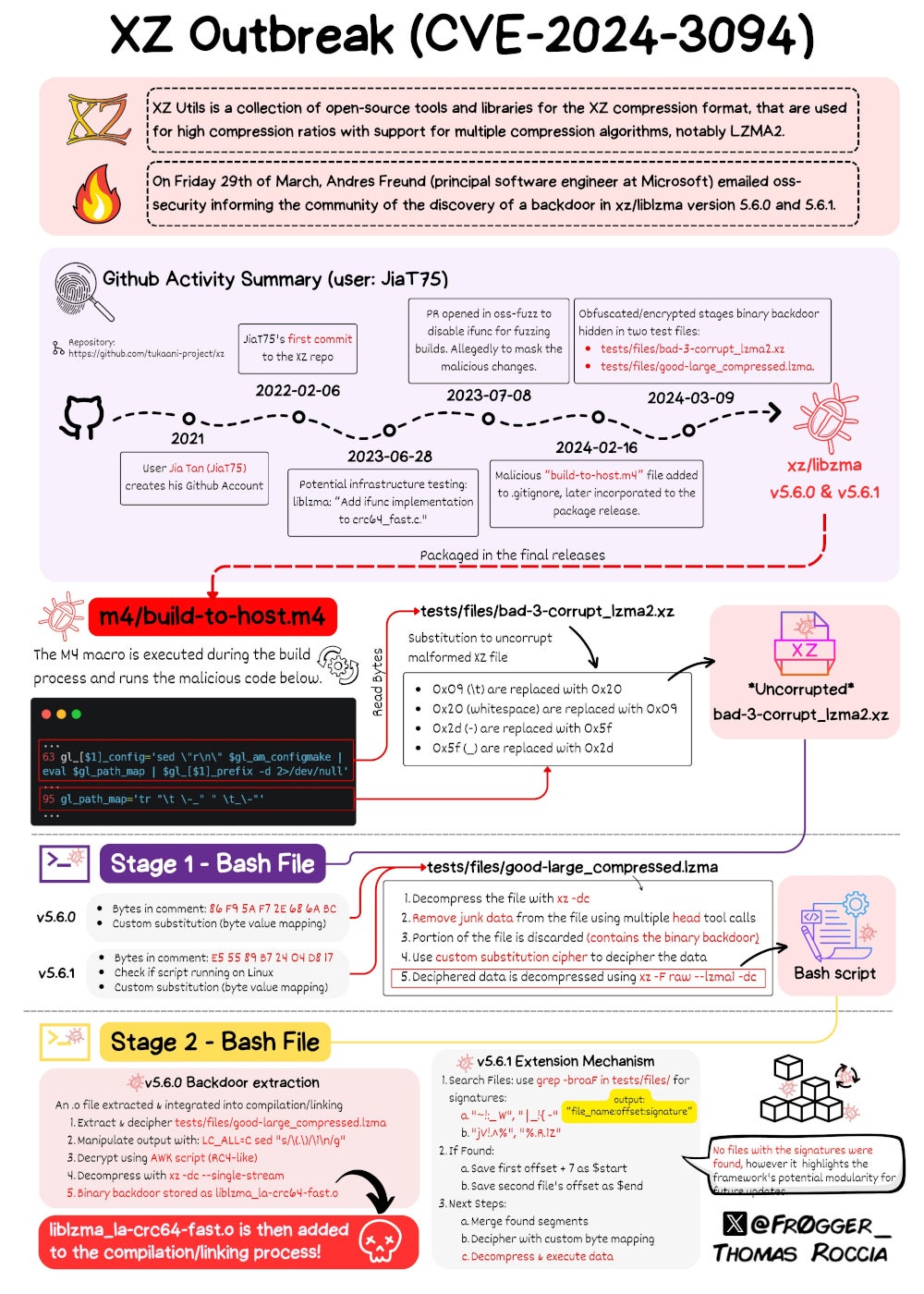 The full CVE-2024-3094 operation. Image: Thomas Roccia
The full CVE-2024-3094 operation. Image: Thomas RocciaThe backdoor is composed of respective parts that person been included implicit aggregate commits connected the XZ Utils GitHub, described successful extent by Freund.
Gynvael Coldwind, managing manager of HexArcana Cybersecurity GmbH,a cybersecurity institution providing consulting and courses services, wrote successful a elaborate investigation of the backdoor that “someone enactment a batch of effort for this to beryllium beauteous guiltless looking and decently hidden. From binary trial files utilized to store payload, to record carving, substitution ciphers, and an RC4 variant implemented successful AWK each done with conscionable modular bid enactment tools. And each this successful 3 stages of execution, and with an ‘extension’ strategy to future-proof things and not person to alteration the binary trial files again.”
DOWNLOAD: Open root speedy glossary from TechRepublic Premium
Martin Zugec, method solutions manager astatine Bitdefender, said successful a connection provided to TechRepublic that “this appears to beryllium a meticulously planned, multi-year attack, perchance backed by a authorities actor. Considering the monolithic efforts invested and the debased prevalence of susceptible systems we’re seeing, the menace actors liable indispensable beryllium highly unhappy close present that their caller limb was discovered earlier it could beryllium wide deployed.”
Which operating systems are impacted by the XZ backdoor?
Thanks to Freund’s discovery, the onslaught was stopped earlier being dispersed connected a wider scale. The cybersecurity institution Tenable exposed the pursuing operating systems known to beryllium affected by the XZ backdoor:
- Fedora Rawhide.
- Fedora 40 Beta.
- Fedora 41.
- Debian testing, unstable and experimental distributions versions 5.5.1alpha-01 to 5.6.1-1.
- openSUSE Tumbleweed.
- openSUSE MicroOS.
- Kali Linux.
- Arch Linux.
In a blog post, Red Hat reported that no versions of Red Hat Enterprise Linux are affected by CVE-2024-3094.
Debian indicated that nary unchangeable mentation of the organisation are affected, and Ubuntu posted that nary released versions of Ubuntu were affected.
MacOS homebrew bundle manager reverted XZ from 5.6.x to 5.4.6, an older yet harmless version. Bo Anderson, maintainer and Homebrew method steering committee member, declared that Homebrew does not “… judge Homebrew’s builds were compromised (the backdoor lone applied to deb and rpm builds) but 5.6.x is being treated arsenic nary longer trustworthy and arsenic a precaution we are forcing downgrades to 5.4.6.”
How to mitigate and support from this XZ backdoor threat
More systems mightiness beryllium affected, particularly those connected which developers compiled the susceptible versions of XZ. Security institution Binarly offers an online detection tool that could beryllium utilized to trial systems to spot if they are affected by the XZ backdoor.
The mentation of XZ should beryllium cautiously checked, arsenic versions 5.6.0 and 5.6.1 incorporate the backdoor. It is advised to revert to a erstwhile known harmless mentation of XZ Utils, specified arsenic 5.4.
Software proviso concatenation attacks are increasing
As previously reported connected TechRepublic, bundle proviso concatenation attacks are progressively being utilized by menace actors.
Yet accustomed bundle proviso concatenation attacks mostly dwell of managing to compromise a cardinal relationship successful the process of the improvement of software, and usage the relationship to propulsion malicious contented to morganatic software, which often gets detected rather rapidly. In the XZ Utils case, it is precise antithetic due to the fact that the menace histrion cautiously managed to summation the spot of morganatic developers and go 1 of the maintainers of the tool, allowing him to dilatory propulsion antithetic susceptible parts of codification into the bundle without being noticed.
Software proviso concatenation attacks are not the lone expanding threats; other proviso concatenation attacks based connected IT products are besides increasing.
Therefore, companies should guarantee that 3rd parties are taken into information successful their onslaught aboveground monitoring.
Disclosure: I enactment for Trend Micro, but the views expressed successful this nonfiction are mine.









 English (US) ·
English (US) ·