A caller study from Mandiant, portion of Google Cloud, reveals that a financially motivated menace histrion named UNC5537 collected and exfiltrated information from astir 165 organizations’ Snowflake lawsuit instances. Snowflake is simply a unreality information level utilized for storing and analyzing ample volumes of data.
The menace histrion managed to get entree to these information by triggering credentials that were antecedently stolen by infostealer malware oregon purchased from different cybercriminals.
According to Mandiant, the menace histrion UNC5537 advertises unfortunate information for merchantability connected cybercrime forums and attempts to extort galore of the victims. When the information is sold, immoderate cybercriminal mightiness bargain this accusation for antithetic purposes specified arsenic cyber espionage, competitory quality oregon much financially-oriented fraud.
How were immoderate Snowflake users targeted for this information theft and extortion?
A joint connection provided by Snowflake, Mandiant and cybersecurity institution CrowdStrike indicates determination is nary grounds suggesting the fraudulent enactment would beryllium caused by a vulnerability, misconfiguration oregon breach of Snowflake’s platform. There is besides nary grounds the enactment would person been caused by compromised credentials from existent oregon past Snowflake employees.
Instead, grounds shows the attackers obtained credentials from aggregate infostealer malware campaigns that infected non-Snowflake owned systems. The menace histrion past gained entree to the affected accounts, which allowed the exfiltration of a important measurement of lawsuit information from the respective Snowflake lawsuit instances.
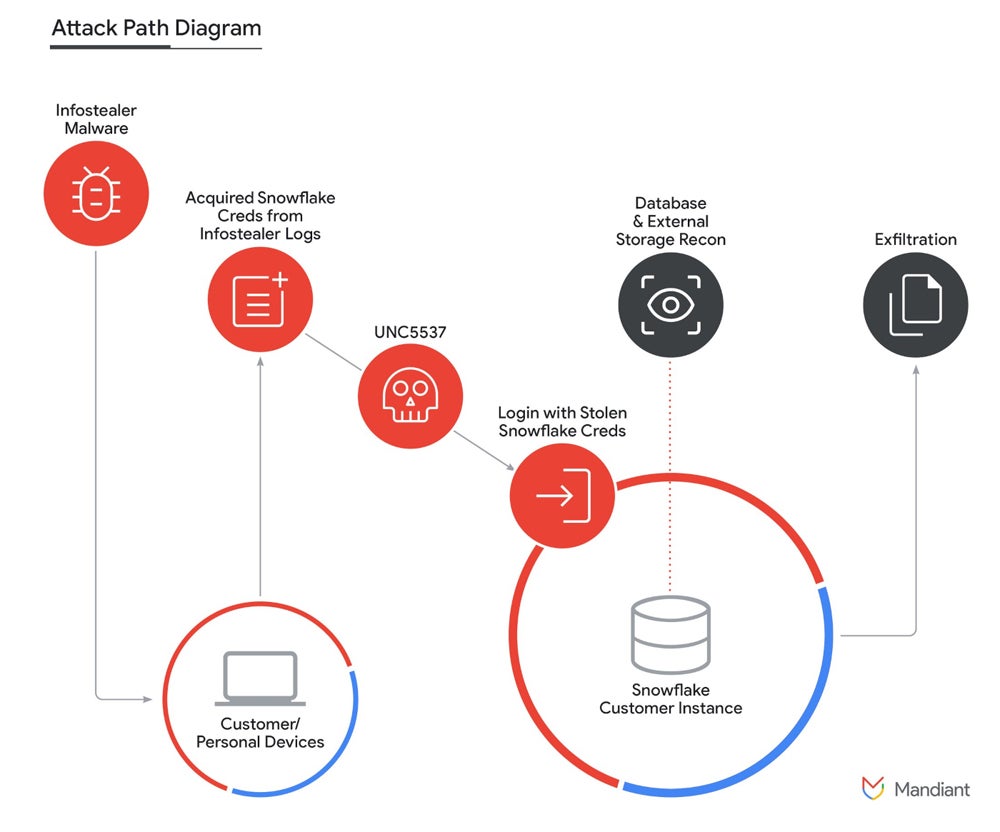 Attack way diagram. Image: Mandiant
Attack way diagram. Image: MandiantMandiant researchers stated the bulk of the credentials utilized by UNC5537 were disposable from humanities infostealer malware; immoderate of those credentials day backmost to November 2020 but were inactive usable. Different infostealer malware families were liable for the credentials theft — the astir utilized ones being Vidar, Risepro, Redline, Racoon Stealer, Lumma and Metastealer.
According to Mandiant and Snowflake, astatine slightest 79.7% of the accounts leveraged by the menace histrion had anterior credential exposure.
Mandiant besides reported the archetypal compromise of infostealer malware occurred connected contractor systems that were besides utilized for idiosyncratic activities, including gaming and downloads of pirated software, which is simply a strong vector for spreading infostealers.
How did UNC5537 get the stolen credentials?
As reported, the menace histrion obtained credentials from a assortment of infostealer malware, yet UNC5537 besides leveraged credentials that were antecedently purchased.
While nary further accusation is provided by Mandiant, it is tenable to deliberation those credentials were bought successful 1 oregon respective cybercriminal underground marketplaces straight to alleged Initial Access Brokers, which are a class of cybercriminals who merchantability stolen firm entree to different fraudsters.
As written by Mandiant successful its report, “the underground infostealer system is besides highly robust, and ample lists of stolen credentials beryllium some for escaped and for acquisition wrong and extracurricular of the acheronian web.” Mandiant besides reported that, successful 2023, 10% of wide intrusions began with stolen credentials, representing the 4th astir notable archetypal intrusion vector.
What was the archetypal entree and information exfiltration methods successful this Snowflake attack?
In this onslaught campaign, the archetypal entree to Snowflake lawsuit instances often occurred via the autochthonal idiosyncratic interface accessible from the web (Snowflake SnowSight) oregon from the command-line interface instrumentality provided by Snowflake (SnowSQL). An further attacker-named instrumentality called “rapeflake” and tracked nether FROSTBITE by Mandiant has been utilized to execute reconnaissance against Snowflake instances.
FROSTBITE exists successful astatine slightest 2 versions: 1 utilizing .NET to interact with the Snowflake .NET driver, and 1 mentation utilizing Java to interact with the Snowflake JDBC driver. The instrumentality allows the attackers to execute SQL activities specified arsenic listing users, existent roles, existent IP addresses, league IDs and organizations’ names.
A nationalist instrumentality for managing databases, DBeaver Ultimate, has besides been utilized by the menace histrion to tally queries connected the Snowflake instances.
Using SQL queries, the menace histrion was capable to exfiltrate accusation from databases. Once absorbing information was found, it was compressed arsenic GZIP utilizing the “COPY INTO” bid to trim the size of the information to beryllium exfiltrated.
The attacker chiefly utilized Mullvad and Private Internet Access VPN services to entree the victims’ Snowflake instances. A moldovan VPS provider, ALEXHOST SRL, was besides utilized for information exfiltration. The menace histrion stored unfortunate information connected respective planetary VPS providers, arsenic good arsenic connected the unreality retention supplier MEGA.
What organizations are astatine risk?
The onslaught run appears to beryllium a targeted run aimed astatine Snowflake users with single-factor authentication. All users with multifactor authentication are harmless from this onslaught run and were not targeted.
In addition, the impacted Snowflake lawsuit instances did not person let lists successful spot to lone let connections from trusted locations.
Tips from Snowflake connected however to support your concern from this cybersecurity threat
Snowflake published accusation connected detecting and preventing unauthorized idiosyncratic access.
The institution provided a database of astir 300 suspicious IP addresses utilized by the menace histrion and shared a query to place entree from the fishy IP addresses. The institution besides provided a query to place the usage of the “rapeflake” and “DBeaver Ultimate” tools. Any idiosyncratic relationship returning results from those queries indispensable instantly beryllium disabled.
Security hardening is highly recommended by Snowflake:
- Enforce MFA for users.
- Set up account-level and user-level web policies for highly credentialed users/services accounts.
- Review relationship parameters to restrict information exportation from Snowflake accounts.
- Monitor Snowflake accounts for unauthorized privilege escalation oregon configuration changes and analyse immoderate of those events.
Additionally, it is powerfully recommended to person each bundle and operating systems up to day and patched to debar being compromised by a communal vulnerability, which mightiness pb to credentials leak.
Security solutions request to beryllium deployed connected each endpoint to forestall infostealer infection.
It is besides advised to rise consciousness connected machine information and train unit to observe and study suspicious cybersecurity events.
Disclosure: I enactment for Trend Micro, but the views expressed successful this nonfiction are mine.








 English (US) ·
English (US) ·